Summary Points
-
Targeted Spear-Phishing Campaign: A sophisticated spear-phishing campaign targets CFOs and financial executives using a legitimate remote access tool, Netbird, with tactics like social engineering and defense evasion techniques to gain persistent access to compromised systems.
-
Multi-Stage Attack Process: The attack begins with a phishing email impersonating a recruiter, leading victims to a CAPTCHA-protected page that downloads malicious scripts to install Netbird and OpenSSH, creating hidden local accounts for continuous remote access.
-
Emerging Phishing-as-a-Service (PhaaS): New PhaaS offerings, like the Haozi kit, have streamlined phishing operations, enabling attackers with low technical skills to launch campaigns easily, thus lowering barriers for cybercriminals and increasing the threat landscape.
- Addressing Online Threats: As phishing tactics evolve, proper user training and awareness of social engineering techniques are crucial for defense, especially as attackers increasingly focus on exploiting human behavior over bypassing technical security measures.
The Core Issue
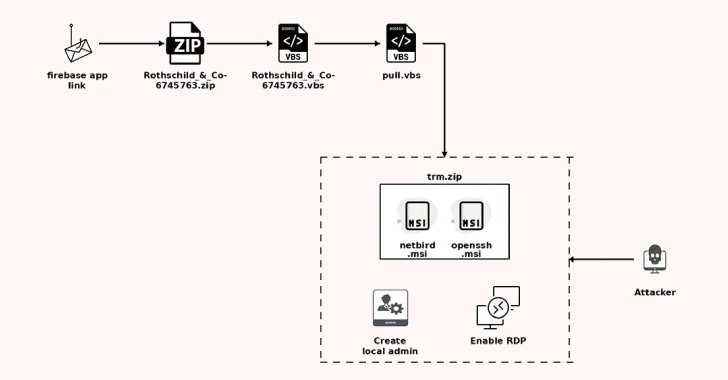
Cybersecurity researchers have uncovered a sophisticated spear-phishing campaign targeting Chief Financial Officers (CFOs) and financial executives across various sectors. This alarming operation, first noted by Trellix in May 2025, employs a legitimate remote access tool called Netbird, which attackers deploy surreptitiously through a multi-stage approach. Initial contact occurs via a phishing email masquerading as a recruitment offer from Rothschild & Co., luring recipients into clicking on a link that leads to an encrypted redirect. This link ultimately enables the download of a malicious ZIP file containing Visual Basic scripts that install Netbird and another tool, OpenSSH, on the victim’s system, establishing covert remote access. Notably, this attack remains unattributed to any known threat actor, highlighting its cunning execution.
Reportedly, the campaign is emblematic of a broader trend wherein adversaries ingeniously leverage legitimate tools to maintain persistence within victim networks, evading detection. Additional phishing tactics utilizing trusted domains and social engineering techniques have emerged concurrently, exemplifying the evolving landscape of cybersecurity threats. As Microsoft elucidates, the rise of Phishing-as-a-Service (PhaaS) platforms exemplifies how burgeoning criminal enterprises are refining their methodologies, effectively lowering the barrier to entry for aspiring cybercriminals. In response, experts emphasize the critical need for enhanced user training and heightened awareness to combat these insidious threats orchestrated by an ever-evolving array of adversaries.
Critical Concerns
This burgeoning spear-phishing campaign poses significant risks not only to the targeted CFOs and their institutions but also extends its ramifications throughout an interconnected ecosystem of stakeholders. Should these financial executives succumb to the meticulously designed lures—which exploit both technological and psychological vulnerabilities—other businesses and organizations could experience direct financial losses, reputational tarnish, and operational disruptions. The infiltration of financial sectors invites the potential for cascading effects: compromised customer data, financial fraud, and disruptions in service—all of which may indirectly impact clients and partners who rely on those businesses. Furthermore, as adversaries increasingly employ sophisticated tactics, including the use of legitimate tools to establish clandestine access, the broader implications for cybersecurity preparedness become pronounced. Organizations lacking robust defense infrastructures may find themselves not only vulnerable to financial losses but also facing erosion of stakeholder trust and regulatory scrutiny, thus amplifying the urgency for enhanced awareness and training aimed at thwarting such intricate, socially-engineered threats.
Fix & Mitigation
In the realm of cybersecurity, especially concerning financial operations, the threat posed by fake recruiter emails targeting CFOs using the ostensibly legitimate NetBird tool cannot be understated. Timely remediation is not merely an option; it is a necessity to safeguard sensitive data and protect organizational integrity across multiple global regions.
Mitigation and Remediation Steps:
- Email Filtering: Implement advanced email security solutions to filter out phishing attempts effectively.
- Employee Training: Regularly educate and train employees, particularly CFOs, on recognizing fraudulent communications.
- Incident Response Plan: Develop a robust incident response plan to address potential attacks swiftly.
- Two-Factor Authentication: Enforce two-factor authentication for sensitive accounts to diminish unauthorized access risks.
- Audit and Monitor: Conduct routine audits and continuous monitoring of unusual account activities.
- Phishing Simulations: Regularly simulate phishing attacks to test and enhance employee awareness and responsiveness.
NIST CSF Guidance:
The NIST Cybersecurity Framework emphasizes the importance of identifying and responding to threats. Organizations should reference NIST SP 800-53 for comprehensive guidelines on security and privacy controls tailored for organizational risk management, particularly concerning email security and incident response strategies.
Advance Your Cyber Knowledge
Stay informed on the latest Threat Intelligence and Cyberattacks.
Understand foundational security frameworks via NIST CSF on Wikipedia.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1