Summary Points
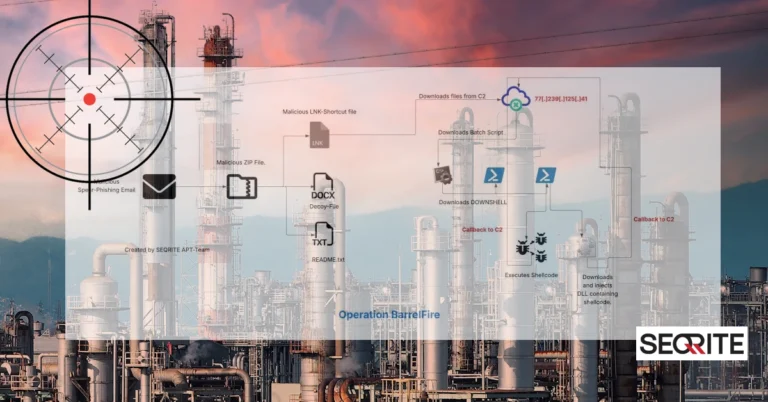
- The threat actor, dubbed Noisy Bear, has been targeting Kazakhstan’s oil and gas sector since April 2025, primarily using spear-phishing with malicious documents mimicking official communications.
- The attacks involve compromised email accounts, urgent messages about salaries, and malicious shortcuts (.LNK files) designed to download additional payloads.
- Noisy Bear’s tactics include the use of PowerShell, open-source post-exploitation tools like Metasploit, and hosting malicious content on sanctioned web providers, with indicators suggesting a possible Russian origin.
- Cyberattacks on the oil and gas industry have surged significantly, with ransomware increases of over 935% year-over-year, driven by automation and persistent security vulnerabilities.
The Core Issue
A newly identified cyber threat group called Noisy Bear has been targeting Kazakhstan’s oil and gas sector since April 2025, with a specific focus on employees at KazMunaiGas, a state-owned energy company. The attackers used sophisticated spear-phishing emails that appeared to be urgent internal messages about salaries and policies, tricking employees into opening malicious attachments. These attachments, disguised as official documents, contained malicious shortcuts that, when opened, downloaded additional malware onto their systems, potentially allowing the hackers to access sensitive information or control critical infrastructure. The emails originated from compromised internal email accounts, making the deceptive messages more convincing. Security researchers suggest that Noisy Bear may be of Russian origin, considering the language use and similarities to other known Russian threat groups. The investigation highlights how threat actors increasingly exploit trusted communications and open-source tools, leveraging the growing digital and automated infrastructure in the energy sector to carry out their malicious campaigns.
The report, compiled by Seqrite Labs’ APT-Team and reported by cybersecurity expert Anna Ribeiro, underscores the major vulnerabilities plaguing vital industries like energy, which have become prime targets amid rising ransomware and espionage campaigns. The group’s activities exemplify how cyber adversaries manipulate corporate trust and employ advanced techniques, such as PowerShell scripts and open-source tools, to infiltrate and expand their reach. The ongoing threat signals a broader trend of escalation in cyber assaults on critical infrastructure, particularly as industries become more dependent on interconnected and automated systems, leaving them exposed to potentially disastrous cyberattacks.
Critical Concerns
The recent emergence of the Noisy Bear threat actor in Central Asia, particularly targeting Kazakhstan’s oil and gas sector, underscores the increasing cyber risks faced by critical infrastructure. This sophisticated group employs spear-phishing campaigns, leveraging compromised employee email accounts and convincingly crafted decoy documents, to infiltrate and infect systems with malware via malicious shortcuts (.LNK files) and PowerShell tools, often hosted on sanctioned web services. Their tactics mimic internal communications to manipulate employees into opening malicious files, leading to potential data breaches, disruption of operations, and intelligence theft. The rise of such targeted attacks, combined with the broader surge in ransomware incidents—reported to have increased by over 935% in the oil and gas industry—heightens the threat landscape, exposing vulnerabilities in automated and outdated security practices. This evolution in cyber espionage and sabotage emphasizes the urgent need for robust defense mechanisms, as these threat actors, possibly of Russian origin, continue to exploit the expanding attack surface of vital energy infrastructure, risking both economic stability and national security.
Fix & Mitigation
Prompt response in addressing cybersecurity threats is crucial for minimizing damage and maintaining organizational integrity.
Mitigation & Remediation
-
Incident Detection: Implement advanced threat detection systems and continuous monitoring to identify unusual activities promptly.
-
Containment Measures: Isolate affected systems immediately to prevent further spread of malware or unauthorized access.
-
Threat Analysis: Conduct thorough investigations to understand the scope, origin, and methods used by Noisy Bear APT group.
-
Security Patches: Apply the latest security updates and patches to all vulnerable systems to close exploited vulnerabilities.
-
User Awareness: Educate employees about phishing and social engineering tactics often used by such malicious campaigns.
-
Network Segmentation: Segregate critical network segments to limit attackers’ lateral movement within the infrastructure.
-
Credential Management: Enforce strong password policies and multi-factor authentication to reduce account compromise risks.
-
Malware Removal: Use specialized tools to thoroughly clean compromised systems and remove persistent threats.
-
Monitoring & Reporting: Continue vigilant monitoring post-remediation and establish clear reporting channels for future incidents.
- Collaboration Efforts: Coordinate with government agencies, industry partners, and cybersecurity communities for intelligence sharing and coordinated response.
Stay Ahead in Cybersecurity
Explore career growth and education via Careers & Learning, or dive into Compliance essentials.
Learn more about global cybersecurity standards through the NIST Cybersecurity Framework.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1