Fast Facts
-
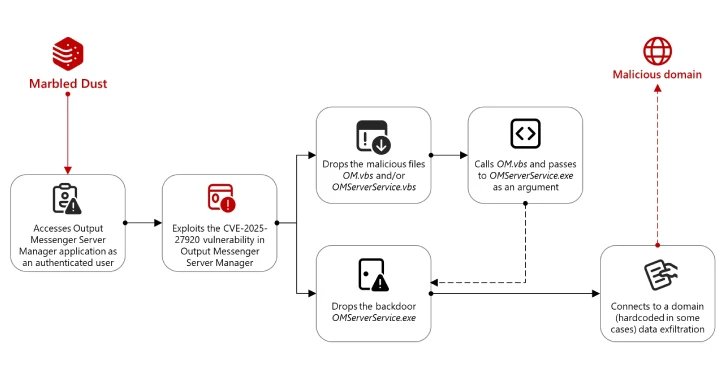
Zero-Day Exploit: A Türkiye-affiliated threat actor, identified as Marbled Dust, has exploited a zero-day vulnerability (CVE-2025-27920) in the Output Messenger platform for cyber espionage since April 2024, targeting Kurdish military entities in Iraq.
-
Attack Methodology: The group uses sophisticated techniques such as DNS hijacking to authenticate to the Output Messenger Server Manager, allowing them to drop malicious payloads and exfiltrate user data.
-
Payload Deployment: The attack involves deploying Golang backdoors like "OMServerService.exe" that connect to a command-and-control domain for data exfiltration, indicating a shift towards more complex attack strategies.
- Increased Sophistication: This incident reflects Marbled Dust’s escalating technical capabilities and operational urgency, marking a significant advancement in their cyber espionage tactics compared to previous activities tracked since at least 2017.
The Issue
In a sophisticated cyber espionage campaign attributed to the Türkiye-affiliated hacking group known as Marbled Dust, a critical zero-day vulnerability (CVE-2025-27920) in the Indian enterprise communication platform, Output Messenger, was exploited. This vulnerability allowed unauthorized remote access to sensitive user data, particularly from targets linked to the Kurdish military in Iraq. The campaign, reported by the Microsoft Threat Intelligence team, highlights a troubling trend of escalating threats in the cyber landscape, as it suggests increased technical sophistication and a more urgent operational focus for Marbled Dust.
Since April 2024, the group has employed tactics such as credential interception through DNS hijacking or typosquatting to gain entry to the Output Messenger Server Manager, allowing them to deploy malicious payloads and exfiltrate user data effectively. Microsoft indicated that the organization had previously targeted entities across the Middle East and North Africa, but this recent breach reflects a notable pivot toward specific geopolitical targets, emphasizing the need for heightened vigilance against increasingly sophisticated adversaries.
Potential Risks
The exploitation of the CVE-2025-27920 vulnerability in Output Messenger by the Türkiye-affiliated threat actor Marbled Dust poses significant risks not only to the direct targets but also to a broader ecosystem of businesses and organizations that utilize similar communication platforms. Should these entities be impacted, they may face severe repercussions, including compromised sensitive data, disruption of their operations, and potential financial losses resulting from a loss of customer trust. Furthermore, the sophisticated nature of this cyber espionage attack indicates that if other organizations were similarly compromised, the ripple effects could lead to widespread instability across sectors reliant on these platforms for secure communications. As a result, an atmosphere of increased vulnerability may prompt clients and stakeholders to reconsider their trust in digital communication channels, thereby undermining competitive advantages and eroding market confidence across entire industries.
Possible Action Plan
In today’s hyper-connected digital landscape, the urgency of timely remediation cannot be overstated, especially when facing sophisticated cyber threats like those executed by Türkiye hackers exploiting the Output Messenger zero-day vulnerability.
Mitigation Measures
- Conduct thorough vulnerability assessments
- Deploy immediate patching protocols
- Implement multi-factor authentication
- Monitor network traffic continuously
- Engage in user education initiatives
- Establish an incident response plan
NIST Guidance Summary
The NIST Cybersecurity Framework (CSF) emphasizes the critical nature of proactive risk management and the importance of timely remediation. Specifically, organizations should refer to NIST Special Publication 800-53 for comprehensive controls relevant to vulnerability management and incident response.
Stay Ahead in Cybersecurity
Explore career growth and education via Careers & Learning, or dive into Compliance essentials.
Access world-class cyber research and guidance from IEEE.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1