Quick Takeaways
- The GPUGate campaign manipulates Google Ads and GitHub to trick users into downloading malware, exploiting trust in both platforms to deliver malicious payloads.
- It employs a novel GPU-gated decryption technique, only decrypting its payload if a physical GPU is detected, making analysis difficult in sandbox environments.
- The malware targets IT professionals and developers in Western Europe, aiming for organizational access to steal credentials, exfiltrate data, or deploy ransomware.
- Once inside, it elevates privileges via PowerShell, establishes persistence, and evades detection by modifying Windows Defender, representing an advanced and ongoing threat since late 2024.
Problem Explained
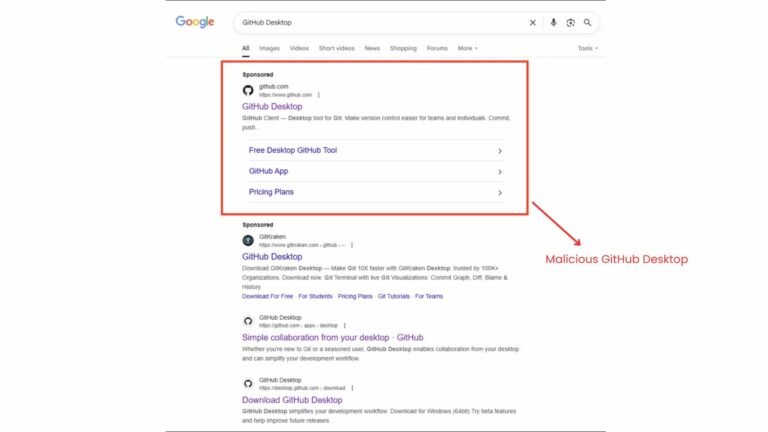
The “GPUGate” malware campaign, believed to be orchestrated by a Russian-speaking cybercriminal group, cunningly exploits trusted platforms like Google and GitHub to deceive users, primarily targeting IT professionals and developers in Western Europe. The attackers launch malicious ads at the top of Google search results for popular tools like “GitHub Desktop,” directing unsuspecting users to fake GitHub repository pages that mimic legitimate ones, but redirect downloads to malicious domains. The attack’s sophistication lies in its use of a large initial file designed to evade security sandboxes and a unique GPU-gated decryption technique: the malware only decrypts if a real GPU with a long device name is detected, thwarting most standard analysis methods performed on virtual machines or short-GPU systems used by security researchers.
Once inside a network, the malware seeks to establish persistent access, using PowerShell scripts to gain administrative rights, create scheduled tasks, and bypass antivirus defenses, with the ultimate aim of stealing credentials, exfiltrating data, or deploying ransomware. The campaign’s strategic use of high-trust platforms and a confluence of technical evasions suggests an evolved effort to infiltrate organizations’ secure environments through seemingly legitimate downloads. Reported by Arctic Wolf’s cybersecurity operations center, this sophisticated attack underscores the growing ingenuity of cyber threats targeting essential software tools and high-privilege user accounts.
Potential Risks
The cyber threat posed by the “GPUGate” campaign exemplifies a sophisticated and evolving malware strategy aimed at compromising organizations, particularly targeting IT professionals in Western Europe. By hijacking trusted platforms like Google Ads and GitHub, attackers craft convincing lure campaigns that direct unsuspecting users to malicious repositories, exploiting user confidence in familiar brands. Their innovative evasion techniques—such as deploying large initial installers designed to bypass sandbox limits and using GPU-driven decryption routines that activate only on genuine, physical GPUs—highlight a deliberate effort to confound detection tools and security analysts. Once inside, the malware employs pre-boot persistence tactics, including elevating privileges with PowerShell and disabling defenses like Windows Defender, to facilitate credential theft, data exfiltration, or ransomware deployment. This campaign’s blend of social engineering, technical sophistication, and targeted focus on high-privilege users underscores a significant risk, emphasizing the need for vigilant defenses and robust security awareness to mitigate impact.
Fix & Mitigation
Prompt
Timely remediation of threats like "GPUGate" malware is crucial to prevent widespread damage, protect sensitive data, and maintain trust in digital platforms. Quickly addressing such threats minimizes the window of vulnerability and reduces the potential for costly security breaches.
Mitigation and Remediation Steps
- Identify Targets: Monitor for unusual spikes or anomalies in Google Ads campaigns and GitHub activity linked to suspicious domains or files.
- Block Malicious Domains: Use firewall rules, browser security settings, and DNS filtering to block known malicious URLs and domains associated with "GPUGate."
- Update Security Tools: Ensure antivirus, anti-malware, and endpoint protection systems are up to date with the latest threat signatures.
- Investigate and Analyze: Conduct forensic analysis on affected systems to understand the payload, infection vectors, and extent of compromise.
- Remove Malware: Safely quarantine or delete identified malicious files, and clean affected systems using appropriate malware removal tools.
- Apply Patches: Update all software, browsers, and plugins to eliminate vulnerabilities exploited by the malware.
- Enhance Monitoring: Increase vigilance through real-time threat detection, network traffic analysis, and anomaly detection systems.
- Educate Users: Inform stakeholders about current threats, phishing tactics, and safe browsing habits to reduce the risk of initial infection.
- Coordinate Response: Collaborate with cybersecurity experts, law enforcement, and the community to share threat intelligence and coordinate containment efforts.
- Review and Improve: Conduct a post-incident review to strengthen cybersecurity policies, incident response plans, and preventative measures.
Continue Your Cyber Journey
Discover cutting-edge developments in Emerging Tech and industry Insights.
Explore engineering-led approaches to digital security at IEEE Cybersecurity.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1