Top Highlights
-
Operation Eastwood: An international coalition led by Europol disrupted pro-Russian hacktivist group NoName057(16) through the dismantling of its server infrastructure and over 100 systems globally, resulting in arrests in France and Spain.
-
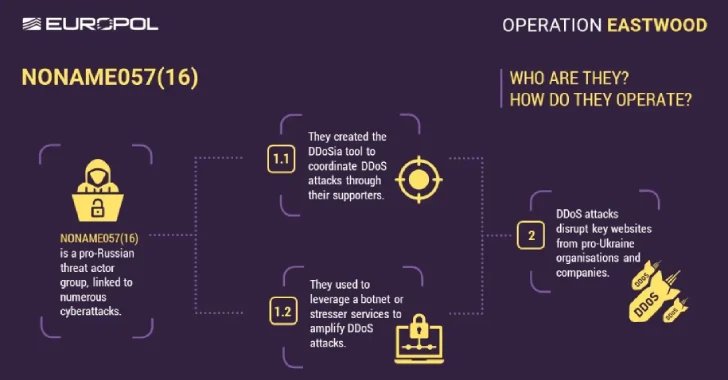
Pro-Kremlin Activities: NoName057(16), operational since March 2022, utilizes Telegram to rally support for DDoS attacks on Ukraine and allies, incentivizing participants via cryptocurrency payments using a program called DDoSia.
-
Most Wanted Allegations: Five Russian nationals, including key figures like Mihail Burlakov and Olga Evstratova, were added to the E.U. Most Wanted list for their roles in orchestrating significant cyber attacks, including optimizing attack software and managing illicit server rentals.
- Evolving Threat Landscape: Russian hacktivist groups are shifting tactics to target critical infrastructure alongside traditional DDoS attacks, indicating a wider collaboration aimed at achieving Russian strategic cyber objectives, with growing activity observed against institutions in Europe.
Key Challenge
In an expansive international operation dubbed Operation Eastwood, Europol has successfully disrupted the infrastructure of NoName057(16), a pro-Russian hacktivist group implicated in numerous DDoS attacks targeting Ukraine and its allies since March 2022. This coordinated effort, executed from July 14 to July 17, involved crackdowns across multiple European nations—including Spain, France, and Germany—resulting in the dismantling of significant server capabilities and the arrest of two suspects, alongside the issuance of warrants for six Russian nationals. Authorities from the Czech Republic to the United States participated in this intricate operation, drawing upon support from various global partners, including Ukraine and Canada.
The collective, NoName057(16), effectively mobilized a network of over 4,000 supporters, enticing them through gamified strategies on Telegram, and incentivizing participation with cryptocurrency payments for DDoS attacks facilitated by a program named DDoSia. Among those identified are key figures like Mihail Evgeyevich Burlakov, accused of playing a pivotal role in optimizing their attack strategies, and Olga Evstratova, linked to enhancing the effectiveness of their software. With the increasing sophistication of Russian cyber operations, the implications of such coordinated disruptions extend beyond mere cybercrime, suggesting a strategic effort to bolster Russian geopolitical objectives amidst ongoing conflicts.
Security Implications
The recent disruption of the pro-Russian hacktivist group NoName057(16) by Europol, while a significant victory in the ongoing battle against cybercrime, poses substantial risks to other businesses, organizations, and users globally. As this group’s infrastructure was dismantled, it precipitates a potential retaliatory cycle; affected entities could experience increased DDoS attacks or be targeted by emergent groups that aim to fill the operational void left by NoName057(16). Moreover, the recruitment strategies employed by such hacktivist collectives, leveraging gamification to entice and mobilize sympathetic individuals, could proliferate across various online platforms, further expanding the threat landscape. Businesses already vulnerable to cyberattacks, particularly in sectors tied to geopolitical tensions, may find themselves under siege as they are roped into larger ideological conflicts beyond their control. As these narrative-driven attacks intensify, the collateral damage could reverberate through supply chains and user bases, eroding trust and stifling economic stability, thereby illustrating a dire need for comprehensive cybersecurity measures and a robust coordination among nations to mitigate these emerging threats.
Possible Actions
Timely remediation is vital in the wake of cyber threats, particularly as observed in Europol’s recent disruption of the NoName057(16) hacktivist group, which has been implicated in DDoS attacks against Ukraine. Such swift action not only minimizes potential damage but also reinforces the resilience of affected entities in the face of ongoing cyber warfare.
Mitigation Steps
- Strengthen Cyber Defenses: Employ advanced firewalls and intrusion detection systems.
- Incident Response Plan: Develop and regularly update a comprehensive incident response strategy.
- Continuous Monitoring: Implement 24/7 network monitoring to detect anomalies in real time.
- Threat Intelligence Sharing: Collaborate with industry partners to share insights on emerging threats.
- Public Awareness Campaigns: Educate stakeholders about risks and best practices in cybersecurity.
- Legal Coordination: Engage law enforcement and legal entities to assist in response and prosecution.
- Patch Management: Regularly update systems to close vulnerabilities.
- Segmentation: Isolate critical infrastructure to limit the scope of attacks.
NIST CSF Guidance
The NIST Cybersecurity Framework (CSF) emphasizes proactive measures and quick recovery methodologies. Specifically, organizations should refer to NIST SP 800-61 for comprehensive guidelines on incident handling and response protocols. This document provides actionable steps that align with best practices in mitigating risks associated with cyber incidents, ensuring a robust defense against threats like those posed by hacktivist groups.
Continue Your Cyber Journey
Explore career growth and education via Careers & Learning, or dive into Compliance essentials.
Access world-class cyber research and guidance from IEEE.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1