Summary Points
- A threat actor, "Chucky_BF," claims to be selling a leak containing over 15.8 million PayPal email and plaintext password pairs, sourced from global accounts.
- The leaked dataset enables credential stuffing, targeted phishing, and increases risks of unauthorized transactions, banking fraud, and identity theft.
- PayPal users should immediately change passwords, enable multi-factor authentication (MFA), and monitor accounts for suspicious activity.
- Industry experts advise urgent updates to security protocols, emphasizing robust password hygiene and proactive breach detection to mitigate potential damages.
The Issue
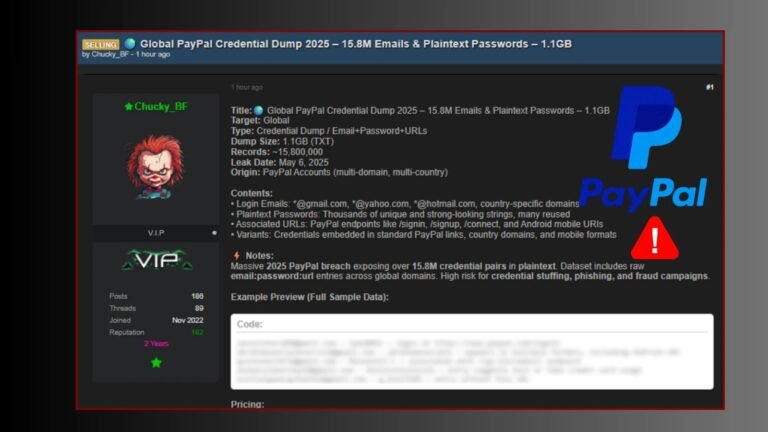
A cybercriminal operating under the pseudonym “Chucky_BF” has allegedly posted on a well-known hacking forum offering a massive dataset purportedly containing over 15.8 million email addresses and plaintext passwords linked to PayPal accounts, claiming it to be a “Global PayPal Credential Dump 2025.” The leaked data, which spans about 1.16GB, reportedly includes sensitive credentials from PayPal accounts worldwide, encompassing various domains and geographic regions. The threat actor boasts that the dataset can be exploited for credential stuffing, phishing attacks, and fraud, providing sample code featuring email, password, and URL combinations that could facilitate large-scale malicious activities. While authorities and cybersecurity experts have not yet verified the authenticity of the leak, industry sources warn of the severe risks posed if the data is genuine, emphasizing the importance of immediate security measures such as changing passwords, enabling multi-factor authentication, and monitoring for suspicious activity.
The report of this breach comes from cybersecurity observers and threat intelligence sources, with some skepticism from experts like Troy Hunt, who noted that the plaintext passwords likely were obtained via other means like credential stuffing or data theft, further complicating the incident’s scope and authenticity. This event highlights the critical need for users and organizations to implement strong password hygiene and advanced security protocols to mitigate the potential damage from such breaches, including unauthorized transactions and identity theft. As the situation develops, security professionals are urging immediate action, including updating breach detection systems and enhancing defenses against social engineering and automated attacks targeting compromised accounts.
Critical Concerns
A cybercriminal known as “Chucky_BF” has claimed to sell a vast dataset consisting of over 15.8 million PayPal email addresses and plaintext passwords, which, if authentic, poses an enormous cybersecurity threat by enabling credential stuffing, targeted phishing, and large-scale fraud. This breach, allegedly sourced from multi-domain PayPal accounts worldwide, could allow attackers to automate login attempts, gain unauthorized access, conduct financial theft, or commit identity fraud—especially if users reuse passwords across sites. The leak includes sensitive credentials linked to common email domains and mobile APIs, increasing the risk of widespread exploitation. While the authenticity of the dump remains unverified, the potential impact underscores the urgent need for PayPal users to change passwords immediately, enable multi-factor authentication, and remain vigilant for phishing and suspicious activity. This incident highlights critical vulnerabilities caused by poor password hygiene and the importance of rapid detection and response to breaches in safeguarding financial and personal data in today’s interconnected digital environment.
Possible Action Plan
Ensuring swift action in response to a threat where a malicious actor claims access to millions of PayPal credentials is crucial to protect user accounts, prevent further data breaches, and maintain trust in the platform. Rapid remediation minimizes potential damage and limits the chance of malicious activity such as identity theft or financial loss.
Containment Measures
- Immediately isolate compromised systems to prevent further unauthorized access.
- Disable affected accounts temporarily to halt ongoing misuse.
- Block suspicious IP addresses and unusual login patterns.
Notification Procedures
- Inform impacted users promptly, advising them to reset passwords and monitor account activity.
- Coordinate with legal and compliance teams to ensure appropriate reporting to authorities and regulators.
Credential Management
- Enforce password resets across all affected accounts with strong, unique passwords.
- Implement multi-factor authentication to enhance account security.
- Conduct a comprehensive review of password storage and security protocols to prevent future leaks.
Security Assessment & Enhancement
- Conduct forensic analysis to determine the breach’s source and scope.
- Patch vulnerabilities and update security measures, including encryption and access controls.
- Initiate regular security audits and staff training on best cybersecurity practices.
Monitoring & Follow-Up
- Establish continuous monitoring for abnormal activities within system logs and user behavior.
- Update security policies and response plans based on findings to improve future preparedness.
Explore More Security Insights
Discover cutting-edge developments in Emerging Tech and industry Insights.
Learn more about global cybersecurity standards through the NIST Cybersecurity Framework.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1