Summary Points
- Microsoft’s Digital Crimes Unit seized 338 domains linked to RaccoonO365, a threat group responsible for stealing over 5,000 Microsoft credentials via phishing kits since July 2024.
- RaccoonO365, also known as Storm-2246, targeted organizations in 94 countries, including more than 2,300 U.S. entities and at least 20 healthcare organizations, using Microsoft-branded fraudulent emails and websites.
- The group, allegedly led by Nigerian hacker Joshua Ogundipe, sold phishing kits on Telegram, earning an estimated $100,000 through at least 200 subscriptions, with investigators tracing transactions via cryptocurrency analysis.
- Microsoft warns that tools like RaccoonO365 accelerate cybercrime, emphasizing the need for global legal cooperation to close loopholes, prevent reemergence, and better combat cross-border cyber threats.
Key Challenge
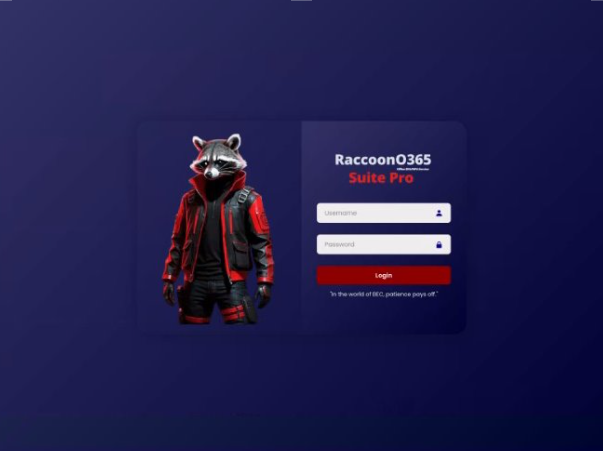
Microsoft’s Digital Crimes Unit (DCU) recently coordinated a major crackdown on RaccoonO365, a cybercriminal group that developed and sold phishing kits used to steal over 5,000 Microsoft account credentials since July 2024. Operating under the alias Storm-2246, this group targeted organizations in 94 countries, with a significant focus on U.S. companies, including more than 2,300 U.S. organizations and at least 20 healthcare entities, through elaborate scams that mimicked Microsoft branding to deceive victims. The threat group, believed to be led by Nigerian developer Joshua Ogundipe, sold access to these malicious tools via a Telegram community of over 850 members, earning at least $100,000 in cryptocurrency. Microsoft identified and traced Ogundipe through blockchain analysis, revealing his role in creating the code that enabled cybercriminals to send thousands of phishing emails daily, often resulting in malware and ransomware attacks. Acted upon court orders, Microsoft worked with cloud and blockchain firms to seize the group’s infrastructure and address international legal challenges, highlighting a growing concern about the rapid proliferation and sophistication of such cyber threats.
The seizure was prompted by Microsoft’s court-ordered collaboration with Cloudflare and Chainalysis, revealing how the group’s service used advanced evasion techniques to bypass security measures, creating fake login pages that captured credentials without triggering multi-factor authentication. Microsoft emphasized that ongoing legal gaps across borders allow cybercriminals like Ogundipe to operate with relative impunity, underscoring the urgent need for global cooperation on cybersecurity laws. The takedown aims to prevent further scams and damages, but Microsoft warns that such threat actors are persistent and often rebuild their operations quickly. The company’s report underscores the evolving landscape of cybercrime, where accessible tools and international crime networks drive an exponential increase in risks to individuals and organizations alike—risks that Microsoft continues to combat through aggressive law enforcement collaboration and technical countermeasures.
Critical Concerns
Microsoft’s Digital Crimes Unit revealed a significant crackdown on RaccoonO365, a cybercrime operation that sold sophisticated phishing kits used by criminals to steal over 5,000 Microsoft credentials across 94 countries since July 2024. This group’s tools, including fraudulent emails, websites, and attachments branding themselves as Microsoft, facilitated a rapid surge in cyberattacks targeting organizations, including at least 2,300 U.S. entities and 20 healthcare facilities, often culminating in malware and ransomware infections. The operation, attributed to Nigerian-born Joshua Ogundipe, involved extensive use of cryptocurrencies for transactions—totaling at least $100,000—highlighting the global reach and financial motivation behind the crime, while showcasing how evolving cybercriminal services leverage anti-analysis features and evasion tactics to bypass security measures. The takedown, achieved through collaboration with Cloudflare and Chainalysis, underscores the persistent, scalable threats posed by accessible, subscription-based phishing tools that exploit legal gaps and challenge international law enforcement efforts, emphasizing the urgent need for coordinated legal frameworks and proactive cybersecurity measures to prevent such operations from fueling exponentially increasing cyber risks with devastating impacts on organizational and personal data security.
Possible Next Steps
Swift action in addressing the seizure of hundreds of phishing sites tied to a large-scale credential theft operation is crucial to minimize damage, recover compromised data, and restore user trust. Timely remediation prevents further exploitation and disruption, safeguarding both organizations and individuals from persistent cyber threats.
Mitigation Strategies:
- Rapid Takedown: Collaborate with domain registrars and hosting providers to swiftly dismantle malicious sites.
- Threat Intelligence Sharing: Distribute detailed information about the phishing campaigns to relevant stakeholders to enhance collective defense.
- User Alerts: Notify users and customers about the phishing tactics and advise on recognizing fraudulent communications.
Remediation Steps:
- Credential Reset: Promptly reset passwords and implement multi-factor authentication for affected accounts.
- Security Patching: Ensure all systems are updated with the latest security patches to prevent exploitation.
- Incident Response: Conduct comprehensive investigations to understand breach scope and prevent recurrence.
- Ongoing Monitoring: Continuously monitor for new phishing attempts and related activities to swiftly respond to emerging threats.
Advance Your Cyber Knowledge
Discover cutting-edge developments in Emerging Tech and industry Insights.
Access world-class cyber research and guidance from IEEE.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1