Fast Facts
-
Targeted Government Institutions: SideWinder has launched a campaign targeting high-level government entities in Sri Lanka, Bangladesh, and Pakistan, including ministries and regulatory authorities, using sophisticated cyber-espionage techniques.
-
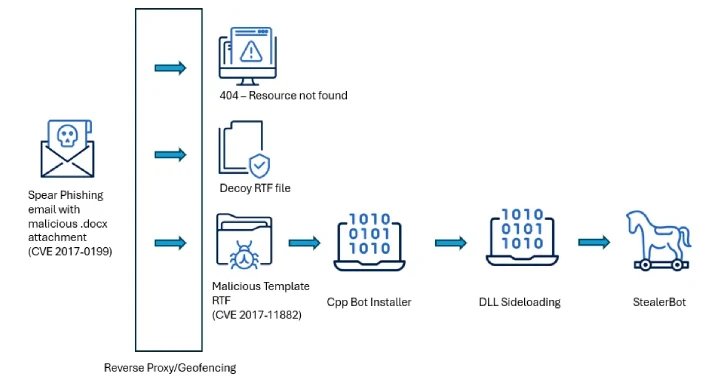
Spear Phishing and Geofencing: The attackers utilize spear phishing emails with geofenced payloads, ensuring malicious content is delivered only to specific regional victims, while non-targeted IP addresses receive decoy files.
-
Exploitation of Legacy Vulnerabilities: The campaign exploits outdated Microsoft Office vulnerabilities (CVE-2017-0199 and CVE-2017-11882) to deploy the StealerBot malware, which enables persistent access and is capable of data exfiltration.
- Operational Continuity and Precision: SideWinder showcases significant operational continuity, characterized by precise targeting and control over malware deployment, acting as a consistent threat in the region’s cyber landscape.
What’s the Problem?
On May 20, 2025, cybersecurity researchers from Acronis reported a sophisticated cyber espionage campaign instigated by the threat actor known as SideWinder, targeting high-level governmental institutions across Sri Lanka, Bangladesh, and Pakistan. The attacks employed refined spear-phishing techniques, utilizing meticulously crafted emails equipped with geofenced payloads, ensuring that only designated victims, such as officials from Bangladesh’s Telecommunication Regulatory Commission and the Central Bank of Sri Lanka, were susceptible to the malicious content. The methodology drew upon well-documented vulnerabilities in Microsoft Office, specifically CVE-2017-0199 and CVE-2017-11882, to facilitate the deployment of StealerBot, a malware that can exfiltrate sensitive data and maintain persistent access in targeted systems.
The researchers highlighted that the operational prowess of SideWinder displayed the group’s sustained commitment and organizational capability, as evidenced by their methodical approach to exploiting remote code execution flaws and their precision in targeting. By deploying malware that leverages DLL side-loading techniques and utilizing a decoy mechanism for unmatched IP addresses, SideWinder ensured the effectiveness of their campaign while evading detection. This blend of strategic targeting and judicious use of technological exploits underscores the evolving nature of cyber threats, particularly within the geopolitical landscape of South Asia.
What’s at Stake?
The recent cyberattacks orchestrated by the SideWinder threat actor against high-level government institutions in South Asia present a material risk not only to the directly targeted organizations but also to the interconnected ecosystem of businesses and users reliant on these entities. Such breaches compromise sensitive data, potentially leading to cascading effects across supply chains and partner networks. As these institutions manage critical functions—from telecommunications to national defense—their incapacitation can disrupt services, erode public trust, and provoke financial instability. Furthermore, the sophistication and precision of SideWinder’s tactics highlight a grave precedent; similar vulnerabilities could be exploited to target other organizations, amplifying the threat landscape. When governmental bodies suffer breaches, the ensuing ripple effect can precipitate heightened regulatory scrutiny and increased operational costs for businesses that interact with these institutions, underscoring the urgency for robust cybersecurity measures across all sectors.
Possible Action Plan
Timely remediation is crucial in safeguarding South Asian ministries from targeted cyber threats, particularly those like the SideWinder APT that exploit outdated vulnerabilities and custom malware.
Mitigation Steps
- Immediate Patching
- Update all software regularly to close exploited vulnerabilities.
- Enhanced Perimeter Security
- Deploy firewalls and intrusion detection systems to block unauthorized access.
- Employee Training
- Conduct cybersecurity awareness programs to recognize phishing attempts and other threats.
- Access Controls
- Implement role-based access to limit data exposure and minimize potential damage.
- Incident Response Plan
- Formulate and regularly test incident response strategies to ensure swift action when breaches occur.
- Network Segmentation
- Isolate sensitive data and critical systems from less secure networks to reduce vulnerability.
NIST CSF Guidance
The NIST Cybersecurity Framework (CSF) emphasizes the need for continuous monitoring and timely responses to identified vulnerabilities. Relevant sections include Identify, Protect, Detect, Respond, and Recover.
For comprehensive remediation details, refer to NIST Special Publication 800-53, which provides a catalog of security and privacy controls tailored for federal information systems but applicable across sectors.
Explore More Security Insights
Discover cutting-edge developments in Emerging Tech and industry Insights.
Access world-class cyber research and guidance from IEEE.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1