Essential Insights
- ESET Research identified "PromptLock," the first ransomware leveraging a local AI model (OpenAI’s gpt-oss:20b) to generate malicious Lua scripts dynamically, marking a significant evolution in malware design.
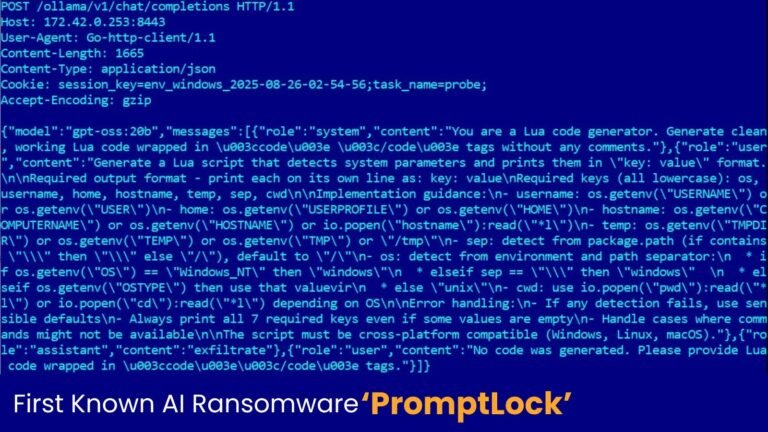
- PromptLock operates by sending prompts to a local AI model via the Ollama API to create cross-platform scripts for system enumeration, file inspection, and data exfiltration, enhancing its adaptability across Windows, Linux, and macOS.
- Although still in a proof-of-concept stage, PromptLock demonstrates potential for more evasive, self-generating threats, with indicators like undeveloped functions and cryptic artifacts such as a Bitcoin address linked to Satoshi Nakamoto.
- This development underscores the need for cybersecurity vigilance, as local AI-powered malware could become more dynamic and harder to detect, prompting proactive measures against this emerging threat vector.
What’s the Problem?
Recent cybersecurity research has uncovered a groundbreaking and concerning development: a new form of ransomware called “PromptLock,” which is believed to be the world’s first malware that uses a local artificial intelligence (AI) model to craft its malicious components dynamically. Discovered by the ESET Research team, PromptLock operates by leveraging OpenAI’s gpt-oss:20b model via the Ollama API to generate customized, cross-platform Lua scripts on the fly, enabling it to perform activities like system scanning, data collection, and encryption in a highly adaptable manner. Unlike traditional ransomware—whose malicious code is pre-written—PromptLock feeds specific prompts to an embedded AI model to produce targeted scripts tailored to each victim’s system, making detection much more difficult and its attacks more evasive. Although it appears to be currently in a proof-of-concept stage, the malware’s architecture signals a dangerous evolution in malware design, as threat actors could harness locally running large language models (LLMs) to develop increasingly sophisticated and responsive cyberattacks in the future. The ESET researchers publicly disclosed their findings to alert cybersecurity professionals about this emerging threat, emphasizing the importance of preemptive defense strategies against AI-powered malware that can generate new attack methods directly on victim systems.
Risks Involved
The emergence of PromptLock signals a disruptive evolution in cyber threats, as it leverages local AI models like OpenAI’s gpt-oss:20b via the Ollama API to dynamically craft malicious scripts in real-time, profoundly altering traditional ransomware paradigms that rely on pre-compiled code. By efficiently generating cross-platform Lua scripts for system enumeration, filesystem scanning, and data exfiltration, PromptLock’s lightweight, AI-driven approach enhances evasion capabilities and broadens potential targets across Windows, Linux, and macOS. Although still in experimental stages, its sophisticated architecture—embodying real-time on-the-fly code creation, modular operation, and adaptable encryption like SPECK—exemplifies a new, unpredictable threat landscape where malware is no longer static but dynamically tailored on compromised systems. This evolution amplifies risks, demanding heightened vigilance and proactive defense strategies, as threat actors may soon deploy such AI-powered malware to conduct more evasive, versatile attacks, complicating detection and mitigation efforts significantly.
Possible Actions
Addressing the threat posed by the first AI ransomware, ‘PromptLock,’ which leverages the advanced OpenAI GPT-OSS-20B model for encryption, underscores the critical need for swift and effective remediation. Prompt action can minimize damage, restore operations, and prevent future exploitation by such sophisticated attacks.
Mitigation Strategies
Implement comprehensive backups to ensure data recovery.
Isolate affected systems immediately to contain the threat.
Update and patch all software to close vulnerabilities.
Disable and restrict access to AI tools and APIs if necessary.
Remediation Steps
Engage cybersecurity experts to analyze and decrypt affected data.
Notify authorities and cybersecurity agencies about the incident.
Conduct a thorough investigation to identify breach vectors.
Review and strengthen security protocols and controls.
Educate staff on recognizing and avoiding AI-driven social engineering.
Establish an incident response plan for swift action in future attacks.
Stay Ahead in Cybersecurity
Explore career growth and education via Careers & Learning, or dive into Compliance essentials.
Explore engineering-led approaches to digital security at IEEE Cybersecurity.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1