Quick Takeaways
-
Non-Human Identities (NHIs) Surge: The rise of AI tools like GitHub Copilot has led to a dramatic increase in non-human identities in corporate environments, with many companies managing 45 machine identities per human user, which significantly complicates secret management.
-
Secrets Sprawl Crisis: GitGuardian’s report indicates that over 23.7 million secrets were exposed on public GitHub in 2024 alone, exacerbated by AI models inadvertently leaking sensitive credentials, especially in LLM deployments.
-
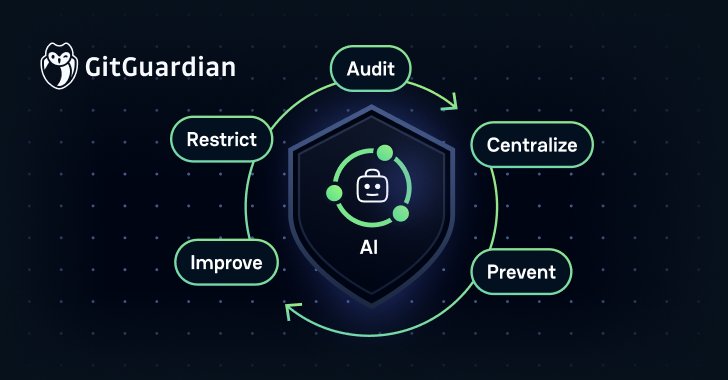
Governance and Controls Essential: To mitigate risks, organizations should implement five key practices: auditing data sources, centralizing NHI management, preventing leaks during LLM deployments, enhancing logging security, and restricting AI data access.
- Prioritize Developer Awareness: Human factors are crucial; fostering communication between developers and security teams ensures that policies and practices are adhered to, enabling safe and efficient AI deployment while managing non-human identity risks effectively.
The Core Issue
The rapid proliferation of artificial intelligence (AI) in enterprise settings has precipitated an alarming surge in non-human identities (NHIs), with statistics revealing that companies now oversee approximately 45 machine identities for every human user. Services like GitHub Copilot and internal chatbots are at the forefront of this transition, driving efficiency but simultaneously leading to mounting security risks. GitGuardian’s 2025 report highlights that over 23.7 million secrets were publicly disclosed through GitHub in 2024 due to improper management of these NHIs. Particularly concerning is the finding that AI-enabled repositories were 40% more likely to leak sensitive information. This alarming trend stems from a lack of stringent policies governing NHIs, resulting in a complex, high-risk network of connections where secrets are often left unrotated, poorly scoped, and forgotten—rendering them vulnerable to malicious actors.
The implications of this NHIs proliferation are increasingly significant, as organizations grapple with the dual challenges of enhancing productivity while safeguarding sensitive information. Key stakeholders in this evolving landscape, notably cybersecurity professionals and developers, must adopt robust governance frameworks to manage NHIs effectively. Effective strategies include auditing data sources for potential leaks, centralizing management practices for NHIs, and reinforcing logging security to prevent the unauthorized disclosure of secrets. As companies navigate these uncharted waters, a proactive approach to AI integration—emphasizing security alongside speed—will be crucial in safeguarding their innovations against inevitable threats, ensuring that advancements in intelligent automation do not come at the cost of fundamental security principles.
Security Implications
The rapid integration of artificial intelligence (AI) into enterprise operations exacerbates the already precarious landscape of non-human identities (NHIs), significantly elevating risks not just for individual organizations, but also for the broader ecosystem of businesses and users. As AI agents proliferate, each requiring unique authentication mechanisms, the sheer volume of digital credentials becomes overwhelming; indeed, many organizations currently manage over 45 NHIs for every human user. This staggering increase in machine identities, coupled with the lax governance surrounding credential management, creates an expansive web of vulnerabilities that attackers can exploit. Furthermore, the inadvertent exposure of sensitive secrets through AI-driven interfaces, such as chatbots, compounds the risk, making confidential information accessible to anyone with the right prompts. If even one organization suffers from a data breach due to these lapses in security, the repercussions can reverberate through interconnected networks, undermining trust and drawing scrutiny that could jeopardize customer relationships and stakeholder confidence across entire industries. Thus, securing NHIs and implementing stringent secrets management protocols is not merely an internal concern; it is a collective imperative that extends to every entity relying on digital infrastructure for operations.
Possible Action Plan
In our rapidly evolving digital landscape, the timely remediation of vulnerabilities becomes paramount in deploying AI securely at scale.
Mitigation Steps
- Conduct Risk Assessments
- Implement Security Protocols
- Ensure Compliance Standards
- Utilize Robust Encryption
- Monitor AI Models Regularly
- Engage in Continuous Training
- Develop Incident Response Plans
- Update Infrastructure
- Foster Collaboration Across Teams
- Stress-test Algorithms
NIST CSF Guidance
The NIST Cybersecurity Framework underscores the necessity of identifying, protecting, detecting, responding to, and recovering from cybersecurity incidents. Particularly, refer to NIST SP 800-53 for comprehensive security and privacy controls tailored to AI deployments, emphasizing the importance of proactive measures in mitigating risks associated with AI technologies.
Advance Your Cyber Knowledge
Stay informed on the latest Threat Intelligence and Cyberattacks.
Explore engineering-led approaches to digital security at IEEE Cybersecurity.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1