Essential Insights
-
Introduction of NightEagle: A new threat actor, NightEagle (APT-Q-95), targeting Microsoft Exchange servers through a zero-day exploit chain is focused on sectors in China such as government, defense, and technology since 2023.
-
Attack Details: NightEagle has rapidly changed its network infrastructure and utilizes a modified version of the Go-based Chisel utility for advanced intranet penetration, enabling intelligence gathering from high-tech and military entities.
-
Trojan Delivery Mechanism: The trojan is delivered via a .NET loader implanted into the Internet Information Server (IIS) of Microsoft Exchange, exploiting a zero-day vulnerability to obtain unauthorized access and read mailbox data.
- Timing and Attribution: The attacks predominantly occur between 9 p.m. and 6 a.m. Beijing time, suggesting a possible North American origin for the threat actor, according to QiAnXin’s findings presented at CYDES 2025.
What’s the Problem?
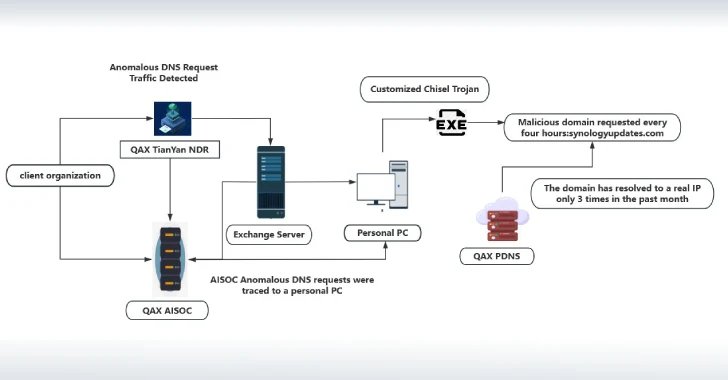
On July 4, 2025, cybersecurity experts unveiled the activities of an enigmatic threat actor dubbed NightEagle (also known as APT-Q-95), which has been targeting Microsoft Exchange servers through a sophisticated zero-day exploit. This shadowy group, active since 2023, has primarily focused on government, defense, and technology sectors within China, conducting cyber espionage to gather sensitive intelligence. The analysis by QiAnXin’s RedDrip Team, presented at the CYDES 2025 conference, revealed that NightEagle operates with remarkable agility, rapidly shifting its network infrastructure to evade detection while executing attacks predominantly during nocturnal hours.
The investigation was prompted by the discovery of a tailored version of the Go-based Chisel tool on a client’s endpoint, indicative of an advanced infiltration strategy. By exploiting a zero-day vulnerability, the attackers compromised the Microsoft Exchange Server’s machineKey, enabling the deployment of a Trojan and unauthorized access to mailbox data. Notably, QiAnXin suggested the perpetrator may be from North America, as attack patterns correlated with nighttime activity in Beijing. As the story unfolds, The Hacker News has reached out to Microsoft for additional insights, indicating an ongoing effort to address this significant cybersecurity threat.
Risks Involved
The emergence of the NightEagle threat actor poses significant risks not only to targeted entities but also to a broader ecosystem of businesses, users, and organizations. Should these attacks proliferate, they could catalyze a chain reaction of cybersecurity breaches, undermining trust in digital infrastructure across sectors reliant on Microsoft Exchange servers. Organizations involved in critical innovation—such as semiconductor manufacturing and AI development—might find sensitive data compromised, leading to intellectual property theft and financial instability. Moreover, the cascading effect of a compromised reputation could deter clients from engaging with firms perceived as vulnerable, exacerbating economic ramifications and potentially resulting in regulatory scrutiny. In essence, the repercussions of such attacks extend far beyond immediate victims, threatening the integrity of entire industries and the confidence of users in digital transactions.
Possible Remediation Steps
In an era where cyber threats evolve incessantly, the expedient addressal of vulnerabilities is paramount, particularly when state-sponsored actors exploit them to target sensitive sectors.
Mitigation Steps
- Patch Deployment: Apply the latest security updates from Microsoft immediately.
- Access Control: Limit access to critical systems based on the principle of least privilege.
- Network Segmentation: Isolate vulnerable systems from the main network to minimize exposure.
- Monitoring and Detection: Implement robust monitoring tools to identify unusual activities indicative of exploitation.
- Incident Response Plan: Develop and rehearse an incident response strategy to efficiently react to breaches.
- User Training: Enhance awareness among personnel regarding phishing and other social engineering tactics.
- Backup Systems: Ensure regular backups of data and systems to facilitate recovery following an incident.
NIST CSF Guidance
The NIST Cybersecurity Framework (CSF) emphasizes continuous risk assessment and swift remediation of vulnerabilities. Specifically, Subcategory PR.IP-3 under the Protection function pertains to the timely application of security patches. For more in-depth guidance, refer to NIST Special Publication 800-53, which outlines security and privacy controls necessary for federal information systems.
Continue Your Cyber Journey
Stay informed on the latest Threat Intelligence and Cyberattacks.
Explore engineering-led approaches to digital security at IEEE Cybersecurity.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1