Essential Insights
-
Cyber Warfare Escalation: The cyber landscape is pivotal for national defense, with cyber espionage and attacks on defense firms being increasingly utilized by nation-states like China and Russia to enhance military operations and intelligence-gathering.
-
Pre-Positioning Strategies: Modern cyber tactics involve pre-positioning access within networks through exploiting zero-day vulnerabilities in edge devices, signifying a shift towards sustained, covert entry methods over traditional destructive attacks.
-
Edge Device Vulnerabilities: Edge devices, including security gateways and VPNs, are prime targets due to their slower patch cycles and public exposure, making them attractive for attackers seeking persistent access to sensitive networks.
-
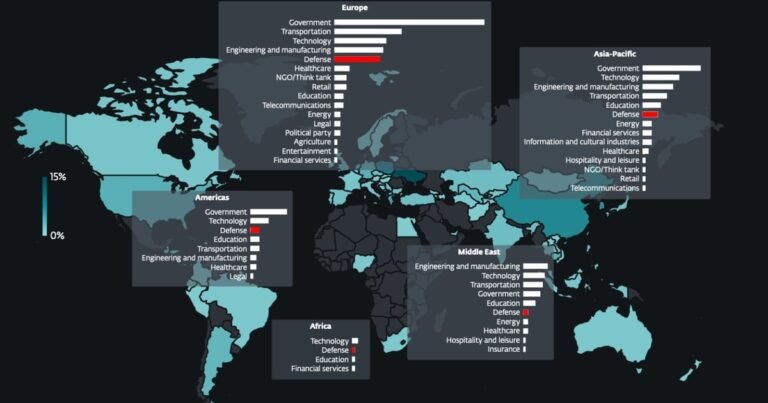
Wide-ranging Targeting Trends: Cyber threats extend beyond the Defense Industrial Base, impacting various sectors, as adversaries increasingly employ similar tactics to infiltrate organizations through public-facing applications and edge exploitation.
Nation-State Attacks on Defense Firms
The cyber domain plays a crucial role in national defense. Recently, experts warned about the rise of cyberattacks targeting the Defense Industrial Base (DIB). In fact, Google reports that hackers linked to China have aggressively targeted defense firms. These attackers exploit vulnerabilities in edge devices to gain access. On another front, Russian hackers have disrupted secure communications, focusing on military operations in Ukraine.
Experts emphasize that nation-states increasingly employ these cyber tactics as a means of influence. Organizations often wrongly assume that being in peaceful relations shields them from threats. Continuous vigilance is now essential. Attackers are not just interested in large, high-profile breaches but in establishing a foothold for long-term intelligence gathering.
Targeting Edge Devices and Workers
Edge devices, like VPN appliances, remain prime targets for cybercriminals. Attackers can exploit these devices to covertly infiltrate systems. Recent data shows that numerous vulnerabilities in edge devices have been discovered and exploited over the past few years. Additionally, North Korean hackers have targeted military agencies, mimicking legitimate companies to steal credentials. Other groups, linked to Iran and China, have sent tailored phishing emails aimed at defense sector workers.
Defense-related organizations have become high-value targets due to their critical roles in national security. Cybersecurity experts urge all enterprises to learn from the DIB’s vulnerabilities. The tactics used against defense firms can also impact other sectors. As attackers seek efficient methods for initial breaches, edge devices present an attractive target, given their frequent exposure to the Internet and often slower patching processes. This situation underscores the importance of robust security measures across all industries.
Discover More Technology Insights
Learn how the Internet of Things (IoT) is transforming everyday life.
Explore past and present digital transformations on the Internet Archive.
CyberRisk-V1