Cybersecurity researchers are calling attention to a series of cyber attacks targeting financial organizations across Africa since at least July 2023 using a mix of open-source and publicly available tools to maintain access.
Palo Alto Networks Unit 42 is tracking the activity under the moniker CL-CRI-1014, where “CL” refers to “cluster” and “CRI” stands for “criminal motivation.”
It’s suspected that the end goal of the attacks is to obtain initial access and then sell it to other criminal actors on underground forums, making the threat actor an initial access broker (IAB).
“The threat actor copies signatures from legitimate applications to forge file signatures, to disguise their toolset and mask their malicious activities,” researchers Tom Fakterman and Guy Levi said. “Threat actors often spoof legitimate products for malicious purposes.”

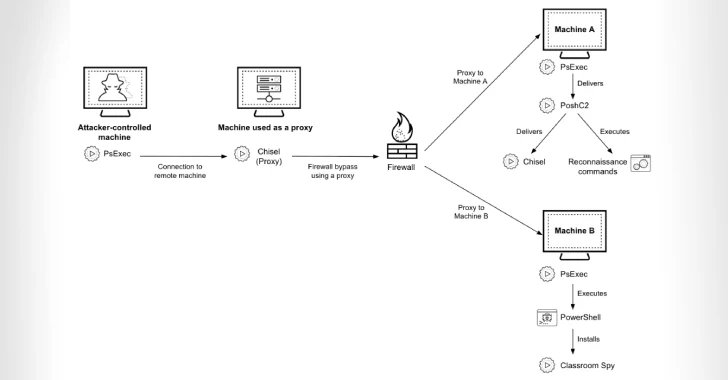
The attacks are characterized by the deployment of tools like PoshC2 for command-and-control (C2), Chisel for tunneling malicious network traffic, and Classroom Spy for remote administration.
The exact method the threat actors use to breach target networks is not clear. Once a foothold is obtained, the attack chains have been found to deploy MeshCentral Agent and later Classroom Spy to commandeer the machines, and then drop Chisel to bypass firewalls and spread PoshC2 to other Windows hosts on the compromised network.
To sidestep detection efforts, the payloads are passed off as legitimate software, using the icons of Microsoft Teams, Palo Alto Networks Cortex, and Broadcom VMware Tools. PoshC2 is persisted on the systems using three different methods –
Setting up a service
Saving a Windows shortcut (LNK) file to the tool in the Startup folder
Using a scheduled task under the name “Palo Alto Cortex Services”
In some incidents observed by the cybersecurity company, the threat actors are said to have stolen user credentials and used them to set up a proxy using PoshC2.

“PoshC2 can use a proxy to communicate with a command-and-control (C2) server, and it appears that the threat actor tailored some of the PoshC2 implants specifically for the targeted environment,” the researchers noted.
This is not the first time PoshC2 has been used in attacks aimed at financial services in Africa. In September 2022, Check Point detailed a spear-phishing campaign dubbed DangerousSavanna that targeted financial and insurance companies located in Ivory Coast, Morocco, Cameroon, Senegal, and Togo to deliver Metasploit, PoshC2, DWservice, and AsyncRAT.

The disclosure comes as Trustwave SpiderLabs shed light on a new ransomware group called Dire Wolf that has already claimed 16 victims across the U.S., Thailand, Taiwan, Australia, Bahrain, Canada, India, Italy, Peru, and Singapore since its emergence last month. The top targeted sectors are technology, manufacturing, and financial services.
Analysis of the Dire Wolf locker has revealed that it’s written in Golang, and comes with capabilities to disable system logging, terminate a hard-coded list of 75 services and 59 applications, and inhibit recovery efforts by deleting shadow copies.
“Although no initial access, reconnaissance or lateral movement techniques used by Dire Wolf are known at this point, organizations shall follow good security practices as well as enable monitoring for the techniques revealed in this analysis,” the company said.