Quick Takeaways
-
Holistic AI Security Platform: Pillar Security offers a comprehensive platform that spans the entire software development lifecycle, aiming to provide trust in AI systems through adaptable defenses and real-time threat detection.
-
Expertise-Driven Foundation: Founded by cybersecurity leaders with both offensive and defensive backgrounds, Pillar combines practical insights to create an effective red team-blue team approach for threat mitigation in AI.
-
Proactive Threat Modeling: The platform begins with the AI Workbench, allowing teams to simulate attacks and align AI usage with security policies before code is written, cultivating security at the design stage.
- Adaptive Guardrails and Sandbox Environments: Pillar enforces adaptive runtime security policies that evolve with emerging threats, while sandboxing techniques isolate AI agents to minimize risks and ensure controlled operation without disruptions.
The Issue
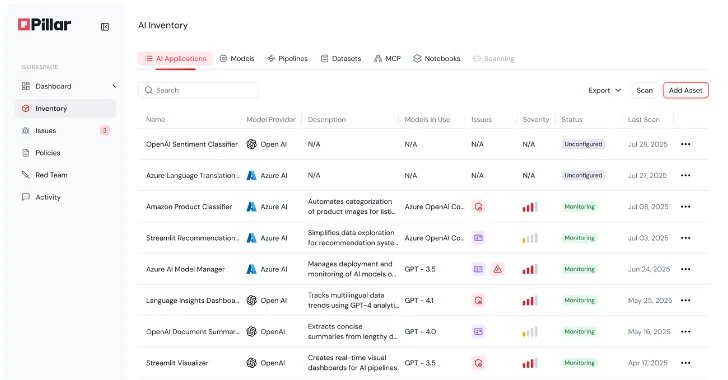
Pillar Security has crafted a comprehensive platform designed to address the myriad challenges of AI security throughout the software development lifecycle. Co-founded by Dor Sarig, with a notable cyber-offensive background, and Ziv Karlinger, a specialist in defensive techniques, the company leverages their combined expertise to create a robust framework for identifying and mitigating security threats. Their platform begins with an innovative AI workbench that facilitates proactive threat modeling even before coding begins, ensuring that AI applications adhere to organizational policies and regulatory standards. By integrating with various development environments and mapping out potential vulnerabilities, Pillar establishes a continuous feedback mechanism that enhances the security posture of applications through adaptive guardrails and real-time monitoring.
This initiative comes at a crucial juncture, as organizations grapple with the complexities of AI, including risks associated with rampant AI utilization—often referred to as AI sprawl. Pillar’s platform sets itself apart with its ability to provide deep visibility into AI assets, conduct real-time telemetry, and execute simulated attacks to preemptively counteract potential threats. Reported by a trusted partner in the technology sector, this account underscores how Pillar Security’s multifaceted, holistic approach not only fortifies AI systems against current threats but also dynamically evolves to anticipate and address future challenges.
Potential Risks
Should a security breach occur within a platform like Pillar Security, the ramifications could reverberate throughout interconnected businesses and users, posing significant risks to operational integrity and user trust. For organizations reliant on AI systems, compromised security can lead to the exposure of sensitive user data, undermining their compliance with regulatory mandates and resulting in financial penalties. Furthermore, the cascading effect could instigate a broader erosion of confidence in AI technologies, thereby stalling innovation and investment across various sectors. Additionally, as third-party applications and integrations come under scrutiny, businesses may face heightened scrutiny and demands for transparency, complicating operational dynamics and potentially destabilizing vendor relationships. Thus, the implications of a single breach extend far beyond immediate financial loss, encapsulating a multifaceted threat landscape that jeopardizes the trust and synergy essential for communal business ecosystems.
Fix & Mitigation
Timely remediation is vital in addressing vulnerabilities to safeguard sensitive data and maintain operational integrity, particularly within platforms like Pillar’s AI Security.
Mitigation Steps
- Regular Vulnerability Assessments
- Automated Threat Detection
- Timely Software Updates
- User Education Programs
- Incident Response Planning
NIST CSF Guidance
NIST CSF emphasizes proactive risk management and establishes a framework for identifying, protecting, detecting, responding, and recovering from incidents. For deeper insights, refer to NIST SP 800-53, which outlines specific security and privacy controls for federal information systems.
Advance Your Cyber Knowledge
Stay informed on the latest Threat Intelligence and Cyberattacks.
Explore engineering-led approaches to digital security at IEEE Cybersecurity.
Disclaimer: The information provided may not always be accurate or up to date. Please do your own research, as the cybersecurity landscape evolves rapidly. Intended for secondary references purposes only.
Cyberattacks-V1